| CPC H04L 63/145 (2013.01) [G06F 16/9024 (2019.01); G06F 16/951 (2019.01); G06N 3/08 (2013.01); H04L 63/1416 (2013.01)] | 20 Claims |
|
1. A method of classifying an element in question comprising:
generating a hypergraph of nodes, edges and neighboring elements by crawling;
generating recursively sets of neighborhoods of the element in question from the hypergraph;
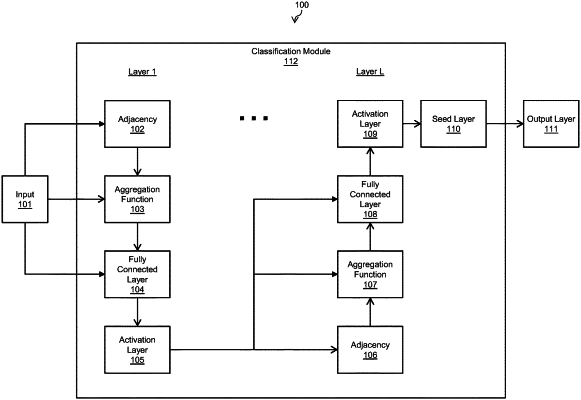
determining a maliciousness level for the element in question by analyzing the sets of neighborhoods with a trained neural network, wherein each layer of the neural network includes two processing steps:
(a) aggregating information from immediate neighbors of each node and using them to calculate additional features for said node;
(b) feeding all features (both original and aggregated from neighbors) into a fully-connected neural layer, one for each node kind;
generating by a profiler a maliciousness level profile for said element in question;
linking information generated by the profiler relating to the element in question and the maliciousness level profile for the element and, for an incriminated file, responding by taking an action or actions such as isolating a machine that received the file, killing processes started by the file, removing persistence of the file on a network or affected computer, cleaning infected samples, modifying risk assessment for computer or network, generating a report, collecting additional artifacts, triggering a search for related elements, blocking a user from taking actions and sending information to other IT or security systems; or for other element types, any of the above actions as applicable, and in addition, other actions specific to particular element types, e.g. blocking an IP address or a web domain from network access, restricting user authorization, blocking access to an external device, shutting down computers, erasing memory devices, filtering e-mail messages, and many more.
|