| CPC H04L 63/1433 (2013.01) [H04L 41/22 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1466 (2013.01)] | 15 Claims |
|
1. A system for performing automated red teaming in an organizational network, the system comprising:
a hardware processor; and
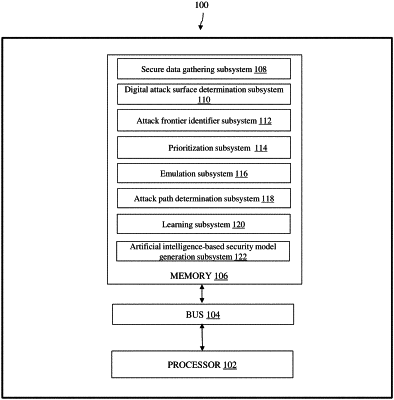
a memory coupled to the processor, wherein the memory comprises a set of program instructions in the form of a plurality of subsystems, configured to be executed by the processor, wherein the plurality of subsystems comprises:
a secure data gathering subsystem configured to obtain an input data and an exit criterion for an organization from one or more data sources via a network, wherein the input data comprises an attack graph and the exit criterion comprises a set of rules;
an attack surface determination subsystem configured to automatically determine one or more attack surface associated with the organization based on the obtained input data and the exit criterion, wherein the one or more attack surfaces comprises least secure points in the organizational network;
an attack frontier identifier subsystem configured to identify one or more attack frontiers for each of the determined one or more attack surfaces, wherein the one or more attack frontiers comprises a set of security attacks to be launched at the determined one or more attack surface;
a prioritization subsystem configured to prioritize each of the identified one or more attack frontiers using one or more pre-defined prioritization strategies;
an emulation subsystem configured to simulate the identified one or more attack frontiers at the determined one or more attack surfaces based on the prioritization;
an attack path determination subsystem configured to determine one or more attack paths associated with at least one of the one or more attack surface based on results of simulation;
a learning subsystem configured to continuously learn attack patterns associated with the determined one or more attack paths based on the results of execution using a plurality of learning techniques; and
an artificial intelligence-based security model generation subsystem configured to generate an artificial intelligence-based security model representing vulnerability of the one or more attack surfaces based on the learnt attack patterns, wherein the artificial intelligence-based security model comprises attack paths correlated with the attack patterns and a risk assessment value associated with each of the one or more attack surface.
|