| CPC H04L 63/1433 (2013.01) [G06F 16/23 (2019.01); G06F 16/9024 (2019.01); H04L 63/102 (2013.01); H04L 63/104 (2013.01); H04L 63/105 (2013.01); H04L 63/20 (2013.01)] | 21 Claims |
|
1. A system for assessing an application access risk, the system comprising:
at least one processor; and
a memory communicatively coupled to the at least one processor, the memory storing instructions executable by the at least one processor to perform a method comprising:
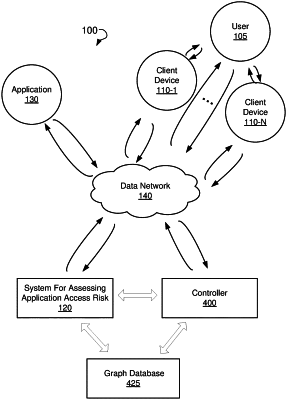
collecting data concerning relationships between an application and one or more client devices in a computing environment;
collecting data concerning relationships between the application and one or more users logged into the one or more client devices in the computing environment;
enriching data related to the one or more client devices with the one or more users logged into the one or more client devices;
updating a graph database including nodes representing the application, the one or more client devices, and the one or more users and edges representing the relationships between the application and the one or more client devices and the relationships between the application and the one or more users;
enriching the graph database by associating the nodes with metadata including information concerning the one or more users accessing the application from the one or more client devices, attributes associated with the one or more users, and permissions associated with the one or more users;
analyzing the graph database to identify a subset of nodes used to access the application;
displaying, via a graphical user interface, a graphical representation of the subset of nodes;
generating allow-list rules identifying at least one user of the one or more users and at least one client device of the one or more client devices permitted to access the application; and
generating an allow-list set of role-based access control permissions to enforce the access.
|