| CPC H04L 63/1433 (2013.01) [G06Q 10/0639 (2013.01); H04L 43/062 (2013.01); H04L 43/0876 (2013.01); H04L 61/5007 (2022.05); H04L 67/53 (2022.05); H04L 63/145 (2013.01)] | 16 Claims |
|
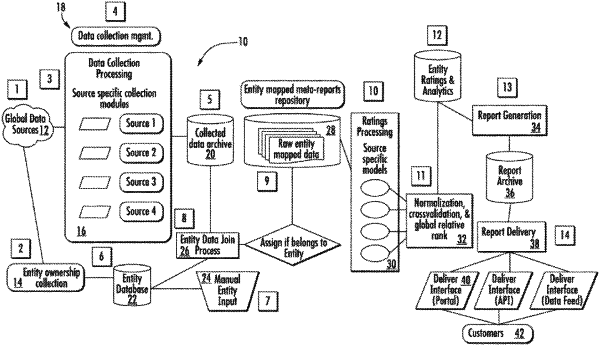
1. A method for determining a security rating of an entity, the method comprising:
determining an internal security rating comprising:
obtaining data indicative of internal security from a plurality of internal data sources;
extracting a plurality of internal security features from the obtained data;
applying a respective transformation function to each of the plurality of internal security features to determine a first plurality of transformed features; and
combining the first plurality of transformed features to form the internal security rating;
determining an external security rating comprising:
obtaining data indicative of external security from a plurality of external data sources;
extracting a plurality of external security features from the obtained data;
applying a respective transformation function to each of the plurality of external security features to determine a second plurality of transformed features; and
combining the second plurality of transformed features to form the external security rating; and
providing, via a reporting facility, a composite security rating for the entity based on the internal security rating and the external security rating, wherein at least one of the internal security features or the external security features indicates malicious activity associated with an IP address of the entity.
|