| CPC H04L 63/1416 (2013.01) [G06F 16/951 (2019.01); G06Q 20/383 (2013.01)] | 20 Claims |
|
1. A method, comprising:
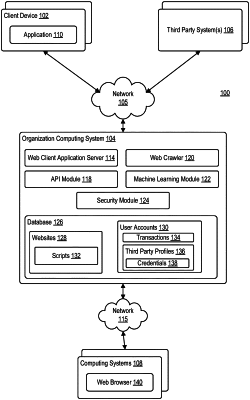
determining, by a computing system, that a third party system has been exposed to a digital security violation;
identifying, by the computing system, a first user account of a user registered with the computing system that has a corresponding account associated with the third party system;
determining, by the computing system, that the user has a second corresponding account with a second third party system;
determining, by the computing system, that the first user account has stored a first set of user credentials for the corresponding account associated with the third party system at a storage location accessible by the computing system;
determining, by the computing system, that the first user account has stored a second set of user credentials for the second corresponding account associated with the third party system at the storage location accessible by the computing system;
launching, by the computing system, a series of web browsers configured to access a first website associated with the third party system and a second website associated with the second third party system;
executing, by the computing system via a first web browser of the series of web browsers, a first automated script specific to the first website associated with the third party system, the first automated script configured to access the corresponding account with the third party system using the first set of user credentials stored at the storage location;
performing, by the computing system via the first web browser, at least one of a plurality of remedial operations with respect to the corresponding account;
executing, by the computing system via a second web browser of the series of web browsers, a second automated script specific to the second website associated with the second third party system, the second automated script configured to access the corresponding account with the second third party system using the second set of user credentials stored at the storage location;
performing, by the computing system via the second web browser, at least one of a plurality of remedial operations with respect to the second corresponding account.
|