| CPC G06F 21/602 (2013.01) [G06F 21/6218 (2013.01); G06F 21/79 (2013.01); H04L 9/008 (2013.01); H04L 9/085 (2013.01); G06F 2221/0751 (2013.01)] | 30 Claims |
|
1. A method for linking encrypted data sets using common encrypted identifiers in an encrypted space, the method comprising:
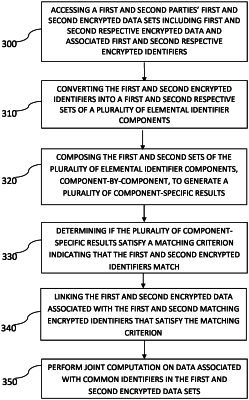
accessing a first and second encrypted data sets independently encrypted by one or more parties, wherein the one or more parties represent one or more respective computing devices, wherein the first and second encrypted data sets comprise first and second respective encrypted data and associated first and second respective encrypted identifiers, and wherein the data and identifiers cannot be unencrypted without one or more secret decryption keys;
converting the first and second encrypted identifiers into a first and second respective sets of a plurality of elemental identifier components, wherein each of the plurality of elemental identifier components in each component set characterizes a distinct numeric property of the corresponding converted encrypted identifier;
composing the first and second sets of the plurality of elemental identifier components, component-by-component, to generate a plurality of component-specific results;
determining if the plurality of component-specific results satisfy a matching criterion indicating that the first and second encrypted identifiers match; and
linking the first and second encrypted data associated with the first and second matching encrypted identifiers that satisfy the matching criterion.
|