| CPC G06F 21/577 (2013.01) [G06F 9/45558 (2013.01); G06F 18/214 (2023.01); G06F 21/54 (2013.01); G06N 20/00 (2019.01); G06F 2009/45587 (2013.01)] | 7 Claims |
|
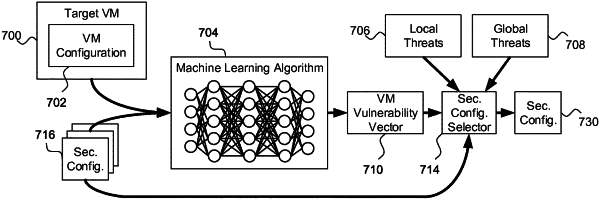
1. A computer implemented method to determine a security configuration for a target virtual machine (VM) in a virtualized computing environment, the method comprising:
training a machine learning algorithm to determine a vector of security vulnerabilities for the target VM based on a vector of configuration characteristics for the target VM, the machine learning algorithm being trained using training examples, each of the training examples including a configuration for a training VM and an associated vulnerability vector based on an observed security occurrence at the training VM, wherein each of the training examples further includes an identification of one of a set of security configurations for the training VM;
selecting at least a subset of the set of security configurations and, for each security configuration in the selected subset, executing the machine learning algorithm with the vector of configuration characteristics for the target VM and an identification of the security configuration in the selected subset, so as to generate a set of vulnerability vectors including a vulnerability vector for each security configuration in the selected subset applied to the target VM; and
selecting a security configuration for the target VM based on the set of vulnerability vectors.
|