| CPC H04W 12/08 (2013.01) [G06F 12/1458 (2013.01); G06N 3/08 (2013.01); G06Q 10/1095 (2013.01); G07C 9/00174 (2013.01); G07C 9/00182 (2013.01); G07C 9/00309 (2013.01); G07C 9/00904 (2013.01); G07C 9/10 (2020.01); G07C 9/21 (2020.01); G07C 9/22 (2020.01); G07C 9/257 (2020.01); G07C 9/27 (2020.01); G07C 9/28 (2020.01); G07C 9/29 (2020.01); H04W 4/027 (2013.01); H04W 4/80 (2018.02); H04W 12/06 (2013.01); H04W 12/64 (2021.01); G07C 2009/00333 (2013.01); G07C 2009/00357 (2013.01); G07C 2009/00769 (2013.01); G07C 2209/08 (2013.01); G07C 2209/61 (2013.01); G07C 2209/63 (2013.01)] | 20 Claims |
|
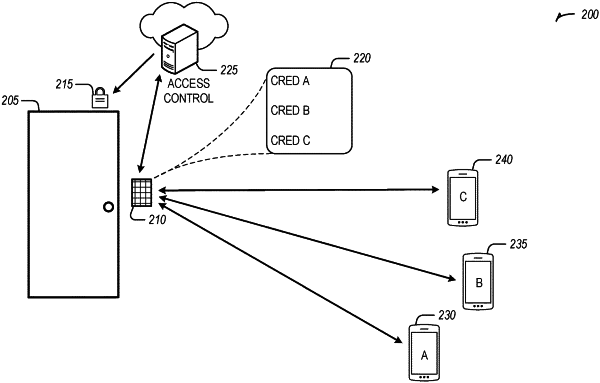
1. A method for regulating access to an asset in an access control system, the method comprising:
receiving a credential of a user from a key device associated with the via a first wireless connection using a low power communication protocol;
establishing a second wireless connection with the key device using Ultra-Wideband (UWB);
determining the user intends to access the asset based on a data set generated based on the second wireless connection, wherein determining the user intends to access the asset comprises:
determining a probability the user intends to access the asset using the generated data set and a trained machine learning model, wherein the trained machine learning model is trained with data sets collected from a plurality of users; and
determining the probability exceeds a predetermined threshold;
providing the credential to an access controller of the access control system for validation in response to determining the user intends to access the asset; and
receiving a validation indication from the access controller and transmitting a command to grant access to the asset.
|