| CPC H04L 9/0825 (2013.01) [H04L 9/0869 (2013.01); H04L 9/3093 (2013.01)] | 7 Claims |
|
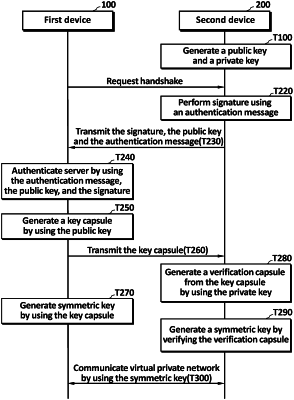
1. A method for forming a virtual private network performed by a first device which includes a processor to form the virtual private network with a second device, the method comprising the steps of:
requesting, by the processor, a handshake for forming the virtual private network;
receiving, by the processor, a signature and a public key;
authenticating, by the processor, the second device by using the signature;
generating, by the processor, a symmetric key by using the public key; and
performing, by the processor, virtual private network communication by using the symmetric key,
wherein generating the symmetric key by using the public key comprises the steps of:
generating, by the processor, a key message by using a random number generator;
generating, by the processor, capsule random value by hashing the key message;
generating, by the processor, a key capsule by capsuling the key message and the capsule random value by using the public key;
transmitting, by the processor, the key capsule; and
generating, by the processor, a symmetric key by using the key capsule,
wherein generating the symmetric key by using the key capsule comprises the steps of:
generating, by the processor, a prekey through a hash for the key message and the public key;
generating, by the processor, key hash value by hashing the prekey and the key capsule; and
generating, by the processor, the key hash value as the symmetric key,
wherein the public key includes a key value which is determined by values of a second key vector, which is generated by a lattice-based algorithm, added to values obtained by multiplying a first key vector, which is generated by the lattice-based algorithm, and a key matrix.
|