| CPC H04L 9/3278 (2013.01) [H04L 9/14 (2013.01); H04L 9/3236 (2013.01)] | 20 Claims |
|
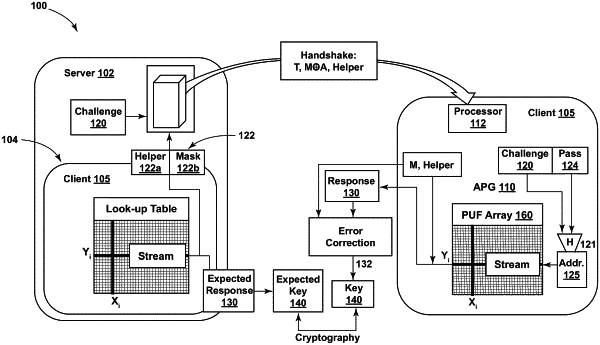
1. A method of generating and using a session key at a server device having a first physical-unclonable-function (“PUF”) array of addressable of PUF devices, comprising:
receiving a first message digest, the first message digest comprising a password that has been iteratively hashed a first predetermined number of times according to a hashing method;
generating, from the first message digest, a series of PUF challenges;
applying the PUF challenges to the first array of addressable PUF devices;
receiving a first response bitstream from the first array of addressable PUF responses corresponding to the PUF challenges;
storing the first response bitstream;
receiving a second message digest, the second message digest comprising the password that has been iteratively hashed a second predetermined number of times by the hashing method, the second predetermined number of times being less than the first predetermined number of times;
iteratively performing the following steps n times until a stop condition is reached:
hashing the second message digest using the hashing method;
generating from the hashed second message a series of PUF challenges;
applying the PUF challenges to the first array of addressable PUF devices;
receiving a response bitstream from the first array of addressable PUF responses corresponding to the PUF challenges; and
comparing the received response bitstream to the first response bitstream, wherein the stop condition is reached when the received response bitstream matches the first response bitstream.
|