| CPC H04L 63/1416 (2013.01) [H04L 63/0876 (2013.01); H04L 63/1425 (2013.01); H04L 63/1466 (2013.01)] | 8 Claims |
|
1. A system for detecting Security Assertion Markup Language (SAML) forgery or manipulation attacks, comprising:
a computing system comprising a memory and a processor;
a policy manager subsystem comprising a first plurality of programming instructions stored in the memory which, when operating on the processor, causes the computing system to:
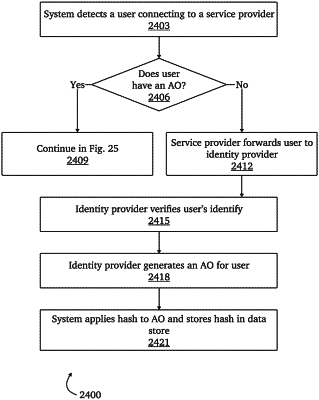
receive a plurality of network packets comprising a first authentication object for a user of a service, the first authentication object comprising a first identification string known to be generated by an identity provider associated with the service;
generate a unique identifier for the first authentication object;
provide the unique identifier to the identity provider from which the first authentication object was generated for inclusion in additional authentication objects issued to the user;
receive a request for access to the service by the user accompanied by a second authentication object comprising a second identification string;
compare a value of the second identification string of the second authentication object against a value of the second identification string of the stored record of the first authentication object;
check the second authentication object for the unique identifier; and
generate an authentication failure if the unique identifier is missing or invalid; and
a hashing subsystem comprising a second plurality of programming instructions stored in the memory of, and operating on the processor of, the computing system, wherein the second plurality of programmable instructions, when operating on the processor, cause the computing system to:
receive authentication objects from the policy manager;
calculate unique identifiers for authentication objects received by performing a plurality of calculations and transformations on each received authentication object; and
return the unique identifiers for authentication objects received to the policy manager.
|