| CPC H04L 9/3236 (2013.01) [G06F 16/2219 (2019.01); G06F 21/31 (2013.01); G06F 21/6227 (2013.01); H04L 63/0815 (2013.01); G06F 2221/2149 (2013.01); H04L 63/0807 (2013.01); H04L 63/0876 (2013.01)] | 20 Claims |
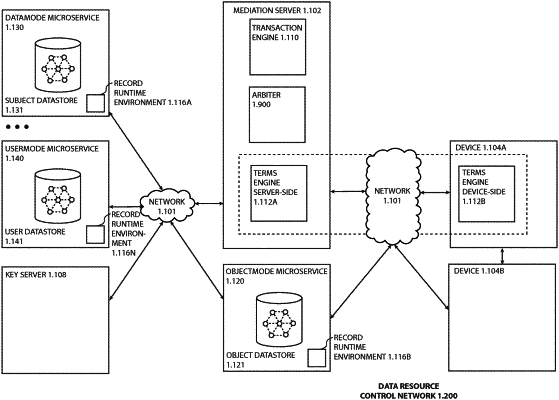
|
1. A method for electronic authentication comprising:
receiving an authentication request from a first device;
receiving an identity claim from at least one of the first device and a second device associated with the first device, the identity claim comprising a device root hash computed by a hash function using inputs comprising a previously calculated hash value of the device;
retrieving data of a user profile associated with at least one of the first device and a user of the first device, the user profile comprising a profile root hash computed by the hash function using inputs comprising a previously calculated hash value of the user profile,
extracting the profile root hash from the user profile associated with at least one of the first device and the user of the first device;
comparing the device root hash with the profile root hash to verify an identity of at least one of the first device and the user of the first device;
determining that the device root hash and the profile root hash of the user profile are not identical; and
denying the authentication request and optionally locking the user profile to deny a prospective authentication request by at least one of the device and the user of the device.
|