| CPC H04L 9/0869 (2013.01) [G06F 21/6209 (2013.01); G06F 21/629 (2013.01); H04L 9/3213 (2013.01); H04L 2209/24 (2013.01)] | 11 Claims |
|
1. A method for performing a search operation, the method comprising:
within a data layer that has a data store and that provides data services to external client applications:
receiving a request to search the data store for a query value;
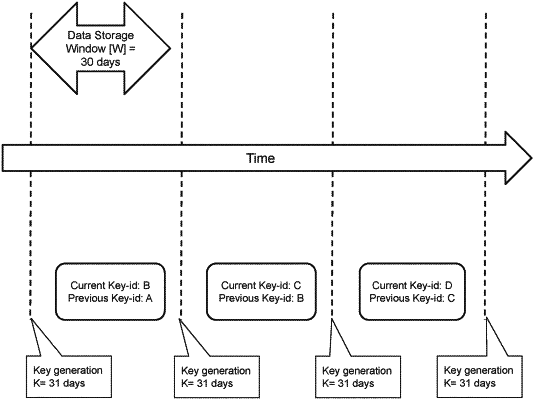
identifying first and second keys, a first column of the data store holding a first encrypted value that was encrypted with the first key, and a second column of the data store holding a second encrypted value that was encrypted with the second key;
selecting one of the first and second keys based at least in part on a difference in time between a current date-time and a date-time of a prior key rotation;
upon selection of the first key, encrypting the query value using the first key, and constructing a first search command with the encrypted query value to be applied to at least one of the first and second columns, executing the first search command, and returning a result based thereon in response to the request to search the data store; and,
upon selection of the second key, encrypting the query value using the second key, and constructing a second search command with the encrypted query value to be applied to at least one of the first and second columns, executing the second search command, and returning a result based thereon in response to the request to search the data store.
|