| CPC H04L 9/0852 (2013.01) [H04L 9/0841 (2013.01); H04L 9/0861 (2013.01); H04L 9/3215 (2013.01)] | 15 Claims |
|
1. A method, comprising:
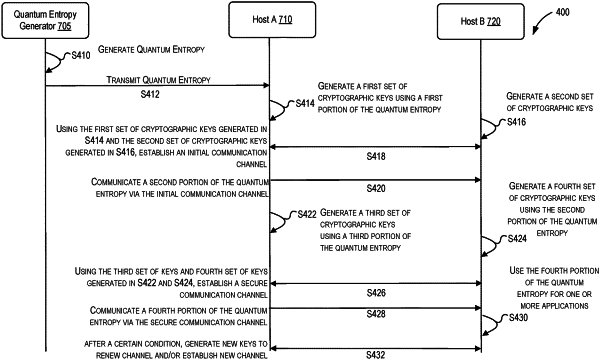
generating, by a second host, a second cryptographic key in preparation for establishing a first communication channel between the second host and a first host, where the first host receives entropy information from an entropy source, the entropy information including a first portion, a second portion, a third portion, and a fourth portion, and where the first host generates a first cryptographic key using the first portion of the entropy information in preparation for establishing the first communication channel between the second host and the first host, wherein the first host is a first computer system or a first virtual machine compute instance running on the first computer system, and the second host is a second computer system or a second virtual machine compute instance running on the first computer system or the second computer system;
establishing the first communication channel between the second host and the first host by performing a first key exchange with the second cryptographic key and the first cryptographic key;
receiving, by the second host, the second portion of the entropy information from the first host using the first communication channel;
generating, by the second host, a fourth cryptographic key using the second portion of the entropy information, where the first host generates a third cryptographic key using the third portion of the entropy information;
establishing a second communication channel between the second host and the first host by performing a second key exchange with the fourth cryptographic key and the third cryptographic key; and
receiving, by the second host, the fourth portion of the entropy information from the first host using the second communication channel established between the second host and the first host.
|