| CPC H04L 9/0825 (2013.01) [H04L 9/0866 (2013.01); H04L 9/3213 (2013.01); H04L 9/3228 (2013.01); H04L 2209/56 (2013.01)] | 20 Claims |
|
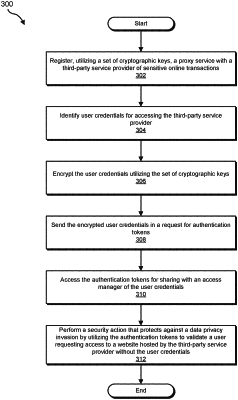
1. A computer-implemented method for protecting the security of authentication credentials utilized to access sensitive data during online transactions, at least a portion of the method being performed by one or more computing devices comprising at least one processor, the method comprising:
registering, by the one or more computing devices and utilizing a set of cryptographic keys, a proxy service with a third-party service provider of sensitive online transactions;
identifying, by the one or more computing devices, user credentials for accessing the third-party service provider;
encrypting, by the one or more computing devices, the user credentials utilizing the set of cryptographic keys;
sending, by the one or more computing devices, the encrypted user credentials in a request for authentication tokens;
accessing, by the one or more computing devices and responsive to the request, the authentication tokens for sharing with an access manager of the user credentials; and
performing, by the one or more computing devices, a security action that protects against a data privacy invasion by utilizing the authentication tokens to validate a user requesting access to a website hosted by the third-party service provider without the user credentials.
|