| CPC H04L 63/1433 (2013.01) [G06F 21/577 (2013.01); G06N 3/02 (2013.01); H04L 41/16 (2013.01)] | 19 Claims |
|
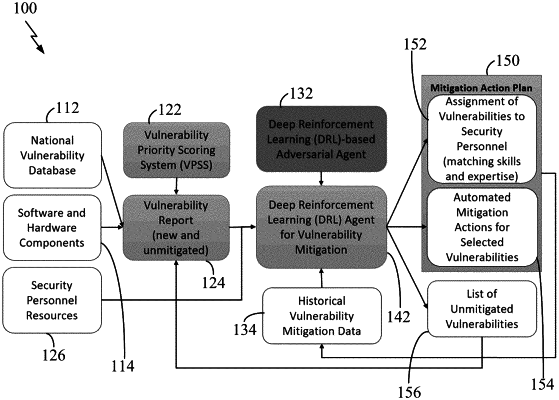
1. A method for mitigating computer and network security deficiencies comprising:
obtaining a vulnerability scan report for a vulnerability on a computer system component;
generating a Vulnerability Priority Scoring System (VPSS) score for the vulnerability based on the vulnerability scan report, wherein the VPSS score is generated by summing a plurality of values based on a qualitative response associated with at least one of factors: a relevance of a network segment in which the vulnerability is reported, a level of existing protection in the network segment, a number of high-value assets in the network segment, or a length of time of the vulnerability residing in the network segment;
developing a vulnerability mitigation policy based on a system state comprising the VPSS score, wherein the vulnerability mitigation policy provides a best action for mitigating the vulnerability selected among one or more trained possible actions by a deep reinforcement learning agent; and
performing the vulnerability mitigation policy based on the best action.
|