| CPC H04L 63/1425 (2013.01) [H04L 63/1433 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A computer-implemented method comprising:
obtaining, from one or more services of a multi-tenant provider network, artifacts resultant from network activity involving a resource, of a user, hosted by the multi-tenant provider network;
detecting, based at least in part on an analysis of one or more of the artifacts and historic activity involving the resource, activity indicative of a potential compromise associated with a client acting as a source of at least some of the network activity;
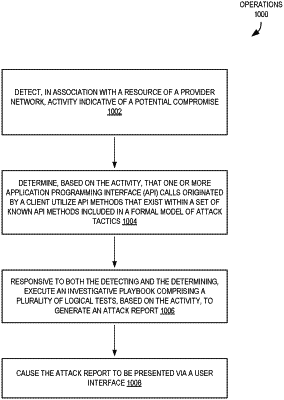
determining, based on the artifacts, that one or more Application Programming Interface (API) calls originated by the client utilize API methods that exist within a set of known API methods included in a formal model of attack tactics;
identifying, based on the network activity, one or more attack tactics;
responsive to both the detecting of the activity indicative of a potential compromise and the determining that the one or more API calls utilize API methods that exist within a set of known API methods, executing an investigative playbook comprising a plurality of logical tests, based on the artifacts, to generate an attack report, the attack report identifying the one or more attack tactics and providing one or more suggested analysis or remediation actions to be performed, within the provider network, to protect against the one or more attack tactics;
causing the attack report to be presented via a user interface; and
causing the user interface to display a graph, generated based on the attack report, to be presented, wherein the graph illustrates one or more clusters, each cluster corresponding to a detected attack tactic and including representations of a set of API call methods.
|