| CPC H04L 63/1416 (2013.01) [H04L 63/1425 (2013.01); H04L 63/1441 (2013.01)] | 21 Claims |
|
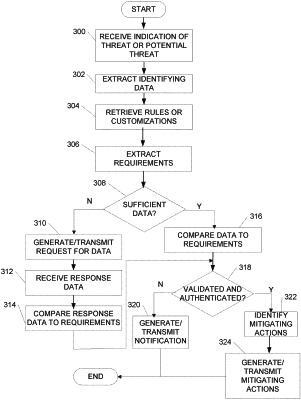
8. A method, comprising:
receiving, by a computing platform and via a secure communication channel, the computing platform having at least one processor and memory, an indication of a threat or potential threat from a first external entity computing system;
extracting, by the at least one processor and from the indication of the threat or potential threat, an identity of a first external entity associated with the first external entity computing system;
retrieving, by the at least one processor and based on the identity of the first external entity, one or more rules or customizations associated with the first external entity;
extracting, by the at least one processor and from the one or more rules or customizations, requirements for authentication and validation of the indication of the threat or potential threat;
comparing, by the at least one processor, information received with the indication of threat or potential threat with the one or more rules or customizations to determine whether sufficient information is included in the information received with the indication of the threat or potential threat;
when it is determined that sufficient information is not included:
generating, by the at least one processor, a request for authentication or validation data;
transmitting, by the at least one processor and via the secure communication channel, the request for authentication or validation data to the first external entity computing system;
receiving, by the at least one processor and from the first external entity computing system and via the secure communication channel, authentication or validation response data; and
comparing, by the at least one processor, the authentication or validation response data to the requirements extracted from the one or more rules or customizations to determine whether the indication of the threat or potential threat is authenticated and validated;
when it is determined that sufficient information is included, comparing, by the at least one processor, the information received with the indication of the threat or potential threat to the requirements extracted from the one or more rules or customizations to determine whether the indication of the threat or potential threat is authenticated and validated;
when it is determined, based on one of: the comparing the authentication and validation response data to the one or more rules or customizations, or the information received with the indication of the threat or potential threat to the one or more rules or customizations, that the threat or potential threat is not validated and authenticated:
generating, by the at least one processor, a first notification indicating that the threat or potential threat is not validated and authenticated; and
transmitting, by the at least one processor and via the secure communication channel, the first notification indicating that the threat or potential threat is not validated or authenticated to the first external entity computing system;
when it is determined based on one of: the comparing the authentication and validation response data to the one or more rules or customizations, or the information received with the indication of the threat or potential threat to the one or more rules or customizations, that the threat or potential threat is validated and authenticated:
identifying, by the at least one processor, one or more mitigating actions;
generating, by the at least one processor, instructions causing execution of the one or more mitigating actions; and
transmitting, by the at least one processor and via the secure communication channel, the generated instructions to one or more devices for execution.
|