| CPC H04L 63/1416 (2013.01) [G06N 20/00 (2019.01); G16B 40/30 (2019.02); H04L 63/0823 (2013.01)] | 20 Claims |
|
1. A system comprising:
one or more computing devices that implement an anomaly detection system, configured to:
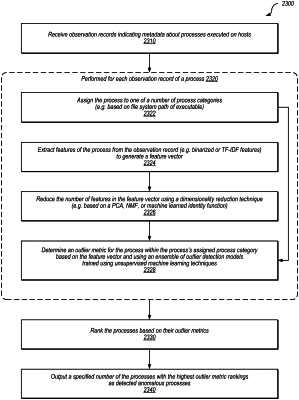
receive a plurality of observation records indicating metadata about a plurality of processes executed on hosts in a computer network, wherein individual ones of the observation records indicate (a) an executable executed by a particular process, (b) a digital fingerprint of the executable, and (c) a certificate used to digitally sign the executable;
for each observation record of a process:
assign the process to one of a plurality of process categories;
extract a plurality of features of the process from the observation record to generate a feature vector; and
process the feature vector using one or more outlier detection models to determine an outlier metric for the process within the process's assigned process category, wherein the one or more outlier detection models are trained using one or more unsupervised machine learning techniques;
rank processes assigned to an individual process category based on outlier metrics of the processes within the individual process category;
detect a set of anomalous processes in the individual process category, wherein the set of anomalous processes are a specified number or percentile of processes in the individual process category that have highest outlier metric rankings; and
output the set of detected anomalous processes.
|