| CPC H04L 63/102 (2013.01) [G06F 3/0622 (2013.01); G06F 3/0664 (2013.01); G06F 3/067 (2013.01); G06F 9/45558 (2013.01); G06F 21/6245 (2013.01); H04L 9/0643 (2013.01); H04L 63/062 (2013.01); H04L 63/08 (2013.01); G06F 2009/45587 (2013.01)] | 20 Claims |
|
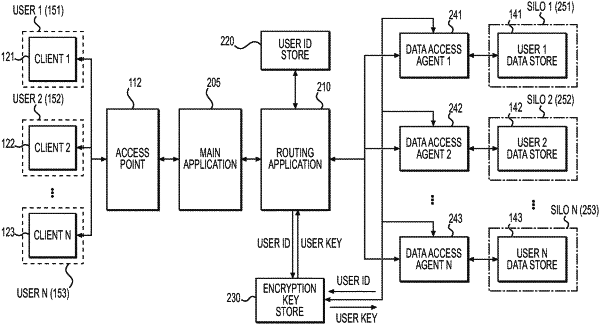
1. A computer-implemented method for secure data access control performed by a data access agent having access to a data store associated with a user, the computer-implemented method comprising:
receiving, by the data access agent from a routing application that lacks access to the data store, a request to retrieve, store, or modify data in the data store, wherein the request includes a first hash generated by the routing application using a hash function of an encryption key that corresponds to an identifier of the user;
in response to receiving the request, retrieving, by the data access agent, the encryption key using the identifier of the user, wherein the identifier of the user is known to the data access agent;
generating, by the data access agent, a second hash using the hash function of the encryption key retrieved in response to receiving the request;
determining, by the data access agent, the second hash generated by the data access agent matches the first hash generated by the routing application and included in the request; and
in response to determining the match, accessing, by the data access agent, the data store to perform the request.
|