| CPC H04L 63/0807 (2013.01) [H04L 63/168 (2013.01)] | 14 Claims |
|
1. A computer-implemented method comprising:
generating, with at least one processor using a ticket-based computer network authentication protocol, a primary key table based on remote system access credentials for a primary domain and at least one secondary key table based on remote system access credentials for at least one secondary domain, wherein the primary key table is associated with a first set of permissions for remotely accessing a computer resource of the primary domain, wherein the at least one secondary key table is associated with at least one second set of permissions for remotely accessing a computer resource of the at least one secondary domain, and wherein the first set of permissions and the at least one second set of permissions are different sets of permissions associated with different permitted actions for remotely accessing computer resources;
merging, with the at least one processor, the primary key table with the at least one secondary key table to form a merged key table, wherein each key of the merged key table comprises an identifier of a domain account associated with an encryption key necessary to encrypt or decrypt a ticket of the ticket-based computer network authentication protocol;
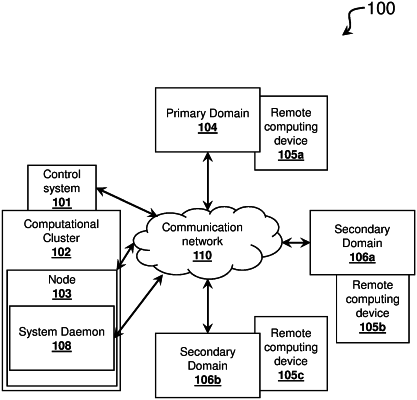
activating, with the at least one processor, a system daemon;
connecting, with the at least one processor and using the ticket-based computer network authentication protocol via the system daemon, a remote computing device of the primary domain and a remote computing device of the at least one secondary domain to a computational cluster;
receiving, with the at least one processor, a first cluster access request to access a first domain account associated with the remote computing device of the primary domain, wherein the first cluster access request comprises a request to perform a first action that is permissible based on the first set of permissions and is not permissible based on the at least one second set of permissions;
authenticating, with the at least one processor, the first cluster access request via the ticket-based computer network authentication protocol;
receiving, with the at least one processor, a second cluster access request to access a second domain account associated with the remote computing device of the at least one secondary domain, wherein the second cluster access request comprises a request to perform a second action that is permissible based on the at least one second set of permissions and is not permissible based on the first set of permissions;
authenticating, with the at least one processor, the second cluster access request via the ticket-based computer network authentication protocol; and
managing, with the at least one processor, access by the computational cluster to the first domain account and the second domain account based on the merged key table, wherein managing access by the computational cluster comprises:
permitting, using the system daemon, access by the computational cluster to the first domain account to perform the first action, based on the first set of permissions of the primary key table in the merged key table; and
permitting, using the system daemon, access by the computational cluster to the second domain account to perform the second action, based on the at least one second set of permissions of the at least one secondary key table in the merged key table.
|