| CPC G06Q 20/34 (2013.01) [G06Q 10/00 (2013.01); G06Q 20/10 (2013.01); G06Q 20/20 (2013.01); G06Q 20/202 (2013.01); G06Q 20/204 (2013.01); G06Q 20/229 (2020.05); G06Q 20/2295 (2020.05); G06Q 20/325 (2013.01); G06Q 20/3674 (2013.01); G06Q 20/40 (2013.01); G06Q 20/409 (2013.01); G06Q 30/00 (2013.01); G06Q 30/0205 (2013.01); G06Q 30/0207 (2013.01); G06Q 30/0222 (2013.01); G06Q 30/0239 (2013.01); G06Q 30/0241 (2013.01); G06Q 30/0255 (2013.01); G06Q 30/0256 (2013.01); G06Q 30/0259 (2013.01); G06Q 30/0261 (2013.01); G06Q 30/0267 (2013.01); G06Q 30/0269 (2013.01); G06Q 30/0273 (2013.01); G06Q 30/0275 (2013.01); G06Q 30/0601 (2013.01); G06Q 30/0609 (2013.01); G06Q 30/0639 (2013.01); G06Q 30/0641 (2013.01); H04L 63/08 (2013.01); H04L 63/0861 (2013.01); H04L 63/107 (2013.01); H04L 67/306 (2013.01); H04M 1/72454 (2021.01); H04M 1/724631 (2022.02); H04W 4/02 (2013.01); H04W 4/021 (2013.01); H04W 4/029 (2018.02); H04W 12/00 (2013.01); H04W 12/02 (2013.01); H04W 12/06 (2013.01); H04W 12/08 (2013.01); H04W 48/04 (2013.01); G06Q 30/0201 (2013.01); G06Q 30/0253 (2013.01); H04M 2203/6054 (2013.01)] | 20 Claims |
|
1. A computer-implemented method comprising:
receiving, by one or more computing systems, a request for user access to a secure location in a building of an entity, the request initiated remotely from the secure location, the user access to the secure location controlled at least in part by a computing device associated with the entity;
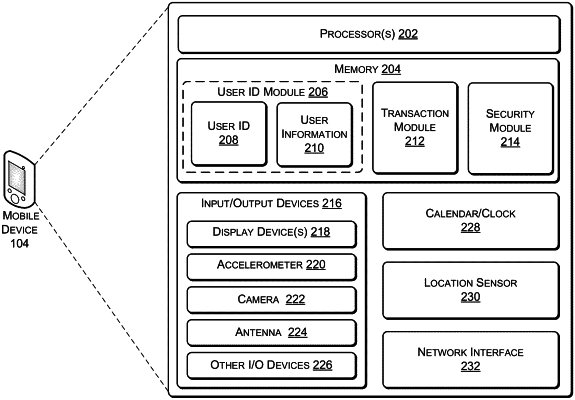
receiving, by at least one of the one or more computing systems and from a mobile device associated with a user, first geolocation data that corresponds to the mobile device;
determining, by at least one of the one or more computing systems, second geolocation data that corresponds to the building, the second geolocation data determined based at least in part on an entity profile associated with the entity;
detecting, by at least one of the one or more computing systems, that the mobile device has arrived to the building based at least in part on a comparison of the first geolocation data and the second geolocation data;
accessing, by at least one of the one or more computing systems and based at least in part on the detecting that the mobile device has arrived to the building, a user profile associated with the mobile device;
determining, by at least one of the one or more computing systems, an authorization of the user access to the secure location based at least in part on the user profile;
generating, by at least one of the one or more computing systems and based at least in part on the authorization, a set of instructions associated with the user access, the set of instructions comprising an electronic code that is generated based at least in part on biometric data available from the user profile, the set of instructions allowing the computing device to provide the user access to the secure location in the building based at least in part on the computing device receiving the set of instructions and on proximity of the mobile device and the computing device; and
sending, by at least one of the one or more computing systems and not by the mobile device, the set of instructions to the computing device, the set of instructions sent after the detecting that the mobile device has arrived to the building.
|