| CPC G06F 21/577 (2013.01) [G06F 11/3089 (2013.01); G06F 11/3664 (2013.01); G06F 11/3672 (2013.01)] | 23 Claims |
|
1. A method for identifying security control steps in software development pipelines, comprising:
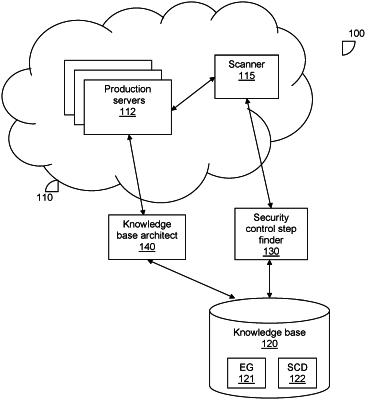
enumerating a plurality of steps in a software development infrastructure by analyzing software development pipeline data of the software development infrastructure, wherein each step includes a set of computer instructions for performing at least one task;
creating a mapping of the software development infrastructure, wherein the mapping includes connections between components of the software development infrastructure, wherein the components of the software development infrastructure include the enumerated plurality of steps;
updating an entity graph having a plurality of nodes representing respective entities of a plurality of entities, wherein each of the plurality of entities corresponds to one of the components of the software development infrastructure, wherein the entity graph is updated to include the nodes representing respective steps of the enumerated plurality of steps;
creating a semantic concepts dictionary, wherein the semantic concepts dictionary defines a plurality of semantic concepts describing potential characteristics of the components of the software development infrastructure;
creating the entity graph based on a plurality of correlations identified between entities of the plurality of entities; and
building a knowledge base using the semantic concepts dictionary and the entity graph;
identifying a plurality of step properties for each of the plurality of steps in step data of the step, wherein at least a portion of the step data is retrieved from the knowledge base; and
classifying at least one of the plurality of steps as a security control step based on the plurality of step properties identified for each of the plurality of steps, wherein each step classified as a security control step includes instructions for at least analyzing code in order to determine whether at least one security requirement is met.
|