| CPC G06F 21/577 (2013.01) [G06F 21/6245 (2013.01); G06Q 30/018 (2013.01); G06F 2221/033 (2013.01); G06F 2221/2101 (2013.01)] | 20 Claims |
|
1. A computer implemented method comprising:
obtaining, from a plurality of evidence sources, security and compliance evidence for an application offered through an interface providing a plurality of different applications for use provided by a computing resource service provider, the plurality of evidence sources comprising:
operational data from the application executing within a runtime environment provided by the computing resource service provider; and at least one of:
a compliance certificate obtained from an independent certification organization; or
a self-attestation generated by a producer of the application;
mapping the obtained security and compliance evidence to risk assessment criteria to generate a risk assessment of the application, the risk assessment criteria comprising a plurality of control sets including indications of potential security and risk vulnerabilities of the application;
generating a representation of the risk assessment across at least a subset of the plurality of controls based on the risk assessment;
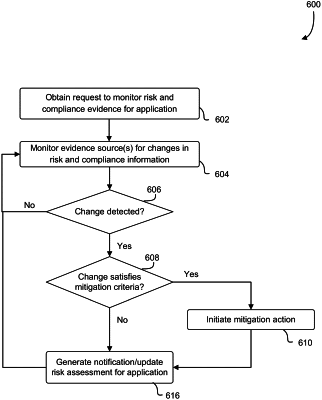
actively monitoring at least one of the plurality of evidence sources for a change in the security and compliance evidence for the application; and
updating the risk assessment representation based on the at least one change detected in the security and compliance evidence for the application.
|