| CPC G06F 21/577 (2013.01) [G06F 8/71 (2013.01); G06F 9/445 (2013.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
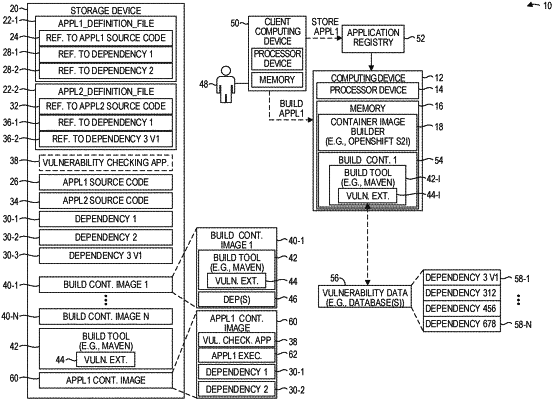
1. A method comprising:
determining, by a container image builder executing on a computing device, that a first container image is to be built;
initiating, by the container image builder, a build container from a build container image;
identifying, by the build container, a first dependency to be incorporated into the first container image;
accessing, by the build container, vulnerability data that identifies a plurality of dependencies that have one or more vulnerabilities;
based on the vulnerability data, determining that the first dependency is devoid of vulnerabilities; and
in response to determining that the first dependency is devoid of vulnerabilities, generating the first container image to include the first dependency.
|