| CPC G06F 21/572 (2013.01) [G06F 9/547 (2013.01); G06F 21/577 (2013.01); G06F 2221/034 (2013.01)] | 19 Claims |
|
16. A managed system for monitoring operations of a managed computing system, comprising:
one or more processors; and
at least one non-transitory computer-readable storage medium having computer-executable instructions stored thereupon which, when executed by the one or more processors, cause the computing system to:
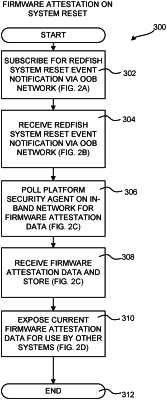
subscribe, by way of a REDFISH-compatible event listener, for notifications that the managed computing system has been reset, wherein:
the notifications are generated by a baseboard management controller of the managed computing system; and
the notifications are transmitted by the baseboard management controller to the management system by way of a first network that is utilized for control of the managed computing system;
receive a notification at the REDFISH-compatible event listener that the managed computing system has been reset from the baseboard management controller by way of the first network;
responsive to receiving the notification that the managed computing system has been reset from the baseboard management controller, transmit a request on a second network for firmware attestation data from a security manager to a platform security agent executing on the managed computing system wherein the second network is utilized for production network traffic, wherein the first network is an out-of-band network that enables the management system to control the managed computing system when the managed computing system is at least one of not reachable via the second network or powered off;
receive the firmware attestation data at the security manager from the platform security agent on the second network; and
expose the firmware attestation data to one or more program components for use in evaluating a trustworthiness of a firmware executing on the managed computing system.
|