| CPC G06F 21/566 (2013.01) [G06F 13/20 (2013.01); G06F 2213/40 (2013.01); G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A computer-implemented method comprising:
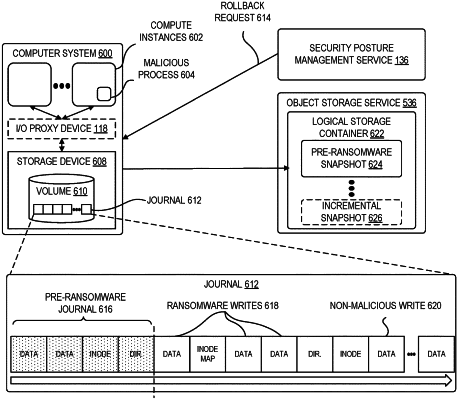
receiving, by an input/output (I/O) proxy device of a computer system coupled to an interconnect of the computer system, a plurality of I/O messages caused by a process running on a guest operating system or a container running on the computer system, wherein the I/O proxy device is coupled to a data storage device storing a storage volume to which the plurality of I/O messages are directed, and wherein the I/O proxy device is further coupled to a control plane of a cloud provider;
identifying, by the I/O proxy device, a pattern within the plurality of I/O messages indicating a ransomware attack;
sending, to a security posture management service of the cloud provider, data indicating detection of the ransomware attack, wherein the data indicating detection of the ransomware attack is sent while the process is performing the ransomware attack;
wherein the storage volume is formatted with a log-structured file system comprising a journal;
wherein the journal, prior to the plurality of I/O messages being caused by the process, comprises pre-ransomware journal entries; and
wherein the journal, after the plurality of I/O messages are caused by the process, comprises ransomware writes that follow the pre-ransomware journal entries in the journal.
|