| CPC G06F 21/554 (2013.01) [G06F 3/0622 (2013.01); G06F 3/0634 (2013.01); G06F 3/0673 (2013.01); G06F 21/33 (2013.01); G06F 21/44 (2013.01); G06F 21/567 (2013.01); G06F 21/568 (2013.01); G06F 3/0659 (2013.01); G06F 2221/031 (2013.01)] | 7 Claims |
|
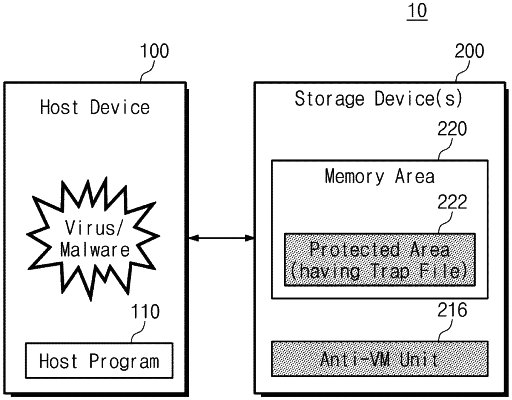
1. A storage device comprising:
a memory area including an area recognizable without authentication of a host device and a protected area that stores a trap file, the protected area configured to be inaccessible to the host device before an authentication operation and to be accessible when the authentication operation with the host device is successful; and
controller configured to control a read/write operation of the memory area in response to receiving an input/output request, to detect malware by analyzing a pattern of data corresponding to the input/output request received from the host device or determining whether the input/output request attempts to access or modulate the trap file, and to initiate a recovery mode when the authentication operation is successful,
wherein the recovery mode includes reading recovery data stored in the protected area and transmitting the recovery data to the host,
wherein the authentication operation is performed when the input/output request attempts to access or modulate the trap file, and
wherein the controller is configured to
detect the malware,
perform the authentication operation when the malware is detected, and
enter a protection mode to protect the memory area or the protected area when the authentication operation is not successful.
|