| CPC G06F 21/54 (2013.01) [G06F 18/214 (2023.01); G06F 18/24147 (2023.01); G06F 21/554 (2013.01); G06F 21/565 (2013.01); G06F 21/568 (2013.01); G06N 20/00 (2019.01)] | 18 Claims |
|
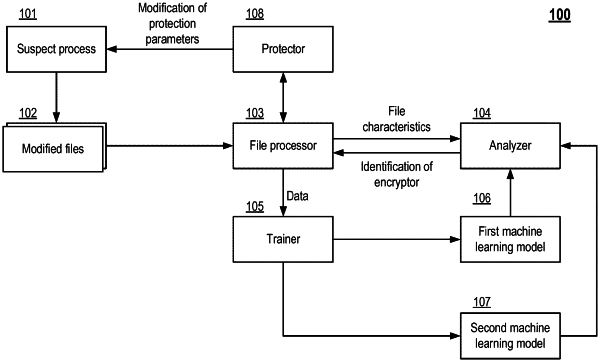
1. A method for identifying a cryptor that encodes files of a computer system, the method comprising:
identifying, by a file processor, one or more files into which a data entry is performed by a suspect process, wherein the identification of the one or more files includes identifying characteristics of each identified file, the characteristics including at least an entropy of at least a part of the file;
for each identified file, determining, by the file processor, characteristics of the identified file;
for each identified file, identifying, by an analyzer, classes of file modifications using a trained machine learning model and respective characteristics of the identified file, wherein the classes of file modifications include at least one class for file modifications made by a cryptor and at least one other class for file modifications made by legitimate software, wherein, for each identified file, the trained machine learning model determines a probability of the modification of the file belonging to one of the classes of file modification;
for each identified file, identifying, by the analyzer, a suspect process as being associated with the cryptor based on the identified classes of file modification of the file;
protecting the computer system from the cryptor;
determining, by the analyzer, a number of the one or more files for which the probability of the modifications of the file by the cryptor exceeds a first threshold; and
when the determined number of the one or more files for which the probability of the modifications of the file exceeds the first threshold is greater than a second threshold, identifying the suspect process as being associated with the cryptor.
|