| CPC H04L 9/0869 (2013.01) [H04L 9/0643 (2013.01); H04L 9/0894 (2013.01)] | 15 Claims |
|
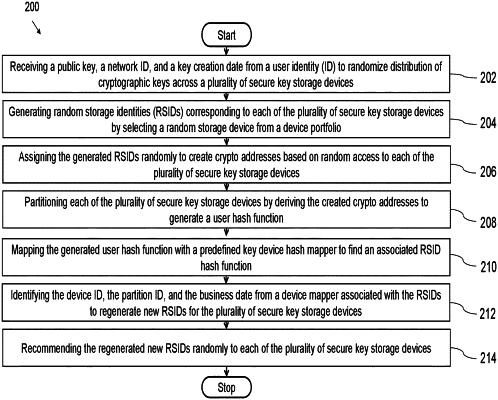
1. A processor-implemented method comprising:
receiving, via an input/output interface, a public key, a network ID, and a key creation date from a user identity (ID) to randomize distribution of cryptographic keys across a plurality of secure key storage devices, wherein each the plurality of secure key storage devices is identified with a respective device ID;
generating, via one or more hardware processors, random storage identities (RSIDs) corresponding to each of the plurality of secure key storage devices by selecting a random storage device from a device portfolio;
assigning, via the one or more hardware processors, the generated RSIDs randomly to create crypto addresses based on random access to each of the plurality of secure key storage devices;
partitioning, via the one or more hardware processors, each of the plurality of secure key storage devices by deriving the created crypto addresses to generate a user hash function based on the user ID, the public key, the network ID, and the key creation date;
mapping, via the one or more hardware processors, the generated user hash function with a predefined key device hash mapper to find an associated RSID hash function;
identifying, via the one or more hardware processors, the device ID, the partition ID, and the business date from a device mapper associated with the RSIDs to regenerate new RSIDs for the plurality of secure key storage devices; and
recommending, via the input/output interface, the regenerated new RSIDs randomly to each of the plurality of secure key storage devices.
|