| CPC H04L 63/1433 (2013.01) | 21 Claims |
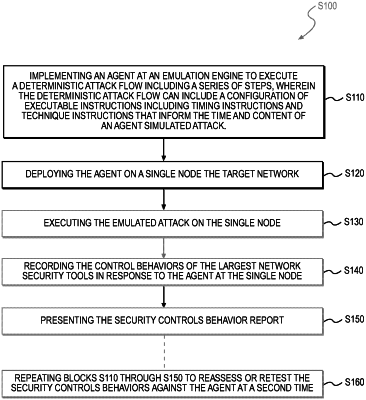
|
1. A method comprising:
accessing an attack graph comprising a set of nodes linked according to a sequence of actions, executed on a machine in a second computer network, representing a known attack on the second computer network, each node in the set of nodes:
corresponding to an action in the sequence of actions;
storing a nominal behavior executable by a target asset to emulate the action; and
storing a set of alternative behaviors analogous to the nominal behavior and executable by the target asset to emulate a transition from a start condition, at the machine prior to start of the action, to an end condition at the machine following completion of the action;
scheduling the target asset, comprising an endpoint device connected to the target network, to automatically execute nominal behaviors and alternative behaviors stored in the set of nodes in the attack graph during a first time period;
accessing a set of alerts generated by a set of security tools, deployed on the target network, during the first time period; and
characterizing a vulnerability of the target network based on presence of alerts, in the set of alerts, indicating detection and prevention of nominal behaviors and alternative behaviors, stored in nodes in the attack graph, executed by the target asset during the first time period.
|