| CPC H04L 63/1425 (2013.01) [H04L 41/14 (2013.01); H04L 41/16 (2013.01)] | 20 Claims |
|
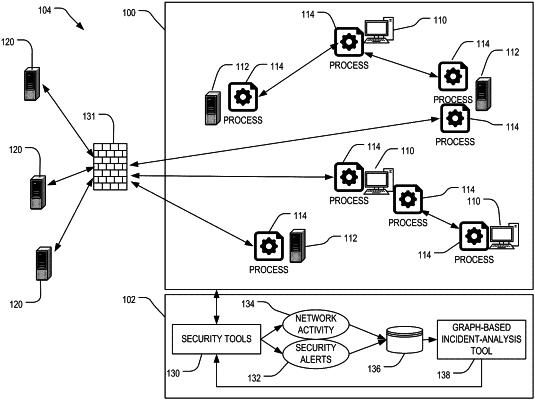
1. A computer-implemented method for analyzing a security incident detected in a computer network, the method comprising executing, by one or more computer processors, instructions for performing operations comprising:
accessing data records of at least one of network activity or security alerts having time stamps within a time period associated with the security incident and pertaining to an organization associated with the security incident;
extracting, from the data records, node data identifying machines within the computer network, processes spawned on the machines, and network destinations external to the computer network connected to by the processes, and edge data identifying relations between the machines and the processes they have spawned and between the processes and the network destinations they have accessed;
generating, based on the node and edge data, a multipartite graph representing the machines, processes, and network destinations as different types of nodes and the relations as edges between the nodes;
identifying, with a graph-based clustering technique, subgraphs within the multipartite graph;
ranking the subgraphs based on at least one of numbers of security alerts or numbers of known indicators of compromise (IoCs) associated with the subgraphs; and
providing an output listing at least a subset of the nodes within one or more highest-ranking subgraphs.
|