| CPC H04L 63/1416 (2013.01) [H04L 63/1425 (2013.01)] | 24 Claims |
|
1. A computing-implemented method, comprising:
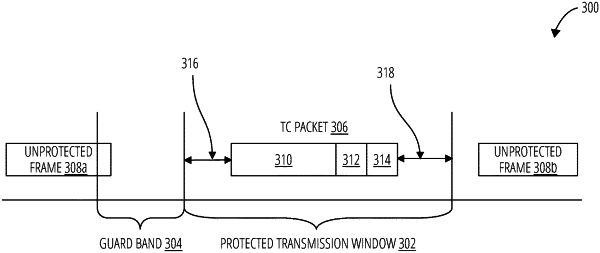
establishing a data stream between a first device and a second device, the data stream comprising a plurality of switching nodes;
providing an indication of a protected transmission window to each of the plurality of switching nodes;
receiving, from one of the plurality of switching nodes, a key performance indicator (KPI) relative to the timing of the protected transmission window for the one of the plurality of switching nodes, wherein the KPI represents a delay time or a time buffer of a packet from the data stream within the protected transmission window; and
determining whether the one of the plurality of switching nodes is subject to a timing attack based on the KPI.
|