| CPC G06F 21/64 (2013.01) [G06F 8/10 (2013.01); G06F 8/41 (2013.01); G06F 21/33 (2013.01); G06F 21/602 (2013.01)] | 20 Claims |
|
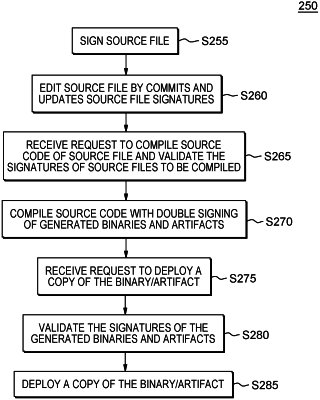
1. A computer-implemented method (CIM) comprising:
creating, by a source code management system, an original version of a set of source code file(s), with the original version of the source code file(s) representing an original version of a computer program;
generating a first plurality of public key infrastructure (PKI) type cryptographic signatures by cryptographically signing, by the source code management system, the original version of the set of source files with a vendor source code signing key;
making a first edit, by the source code management system, to the original version of the set of source file(s) by a commit operation to obtain an edited version of the set of source file(s) representing an edited version of the computer program;
updating the first plurality of PKI type cryptographic signatures when the original version of the set of source code file(s) are edited through one or more commits;
receiving, by a compiler, a request to compile of the edited version of the set of source file(s); and
responsive to receipt of the request, verifying, by the compiler, the updated first plurality of PKI type cryptographic signatures; and
responsive to a successful verification of the first plurality of PKI type cryptographic signatures, generating binaries and artifacts by compiling, by the compiler, the edited version of the set of source file(s); and
generating a second plurality of PKI type cryptographic signatures by cryptographically signing, by the compiler, the binaries and artifacts with a vendor compilation signing key; and
generating a third plurality of PKI type cryptographic signatures by cryptographically signing, by the compiler, the binaries and artifacts with an inbuilt compiler key; and
receiving a request to deploy the generated binaries and artifacts; and
verifying both the second and third plurality of PKI type cryptographic signatures; and
responsive to a successful verification of both the second and third plurality of PKI type cryptographic signatures, deploying the generated binaries and artifacts.
|