| CPC G06F 21/6227 (2013.01) [G06F 11/1464 (2013.01); G06F 16/2379 (2019.01); G06F 2201/84 (2013.01); G06F 2221/2107 (2013.01)] | 20 Claims |
|
1. A computer-implemented method when executed by data processing hardware causes the data processing hardware to perform operations comprising:
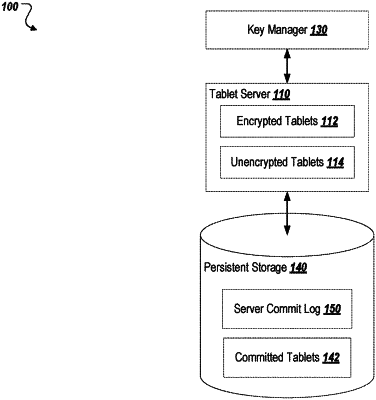
receiving first unencrypted data to write to an encrypted tablet, the encrypted tablet storing encrypted data;
prior to writing the first unencrypted data to the encrypted tablet, generating a first log entry in a commit log for logging the write of the first unencrypted data to the encrypted tablet, the first log entry comprising:
a first unencrypted header; and
an encrypted payload comprising the first unencrypted data encrypted with an encryption key;
receiving second unencrypted data to write to an unencrypted tablet, the unencrypted tablet storing unencrypted data;
prior to writing the second unencrypted data to the unencrypted tablet, generating a second log entry in the commit log for logging the write of the second unencrypted data to the unencrypted tablet, the second log entry comprising:
a second unencrypted header; and
an unencrypted payload comprising the second unencrypted data;
prior to writing the first unencrypted data to the encrypted tablet, identifying a data failure associated with the encrypted tablet; and
based on identifying the data failure associated with the encrypted table, restoring the encrypted tablet using the first log entry and the second log entry of the commit log, the encrypted tablet comprising the first unencrypted data after restoration.
|