| CPC G06F 21/602 (2013.01) [G06F 21/6218 (2013.01); G06F 21/71 (2013.01); G09C 1/00 (2013.01); H04L 9/0866 (2013.01); H04L 9/0877 (2013.01); H04L 9/30 (2013.01); H04L 9/3231 (2013.01); G06F 21/32 (2013.01); H04L 2209/125 (2013.01)] | 20 Claims |
|
1. A system on a chip (SoC), comprising:
one or more processors; and
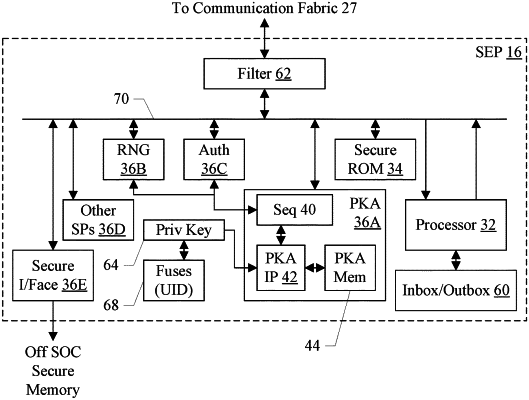
a security circuit that includes a cryptographic accelerator circuit isolated from the one or more processors, wherein the cryptographic accelerator circuit is configured to:
perform a cryptographic operation responsive to a service request associated with the one or more processors, wherein performance of the cryptographic operation includes accessing key material stored in an internal memory of the cryptographic accelerator circuit; and
after performing of the cryptographic operation, zero the key material in the internal memory of the cryptographic accelerator circuit.
|