| CPC G06F 21/577 (2013.01) [G06F 2221/034 (2013.01)] | 20 Claims |
|
1. A computer-implemented method comprising:
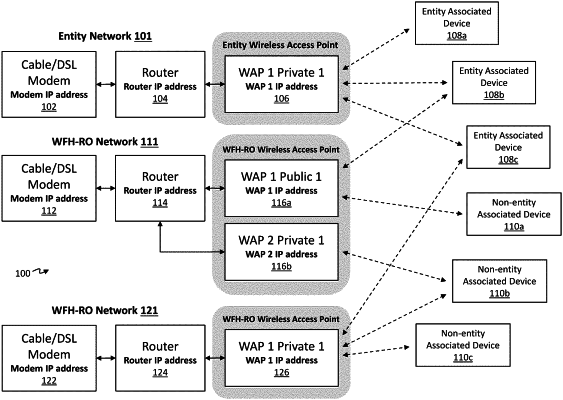
obtaining, for at least one computer network of a plurality of computer networks associated with an entity, a first network dataset;
obtaining, for at least one computer network of a plurality of computer networks not associated with the entity and providing access to the at least one computer network of the plurality of computer networks associated with the entity, a second network dataset;
combining the first and second network datasets to form a combined dataset comprising a plurality of entries, wherein each entry comprises a device identifier, a network identifier, and a timestamp identifier;
obtaining a plurality of Internet Protocol (IP) addresses associated with the entity;
obtaining a plurality of IP addresses associated with a plurality of entities unrelated to the entity, wherein the entity and the plurality of entities unrelated to the entity are each associated with a unique identifier (UID);
for each of the plurality of entries, if the respective network identifier of the entry corresponds to a threshold number of associated UIDs, removing the entry from the combined dataset to form a filtered dataset;
determining, based in part on the IP addresses associated with the entity, whether each of the plurality of computer networks not associated with the entity comprises a remote office network of one or more remote office networks associated with the entity based on the filtered dataset; and
assessing a cybersecurity state of the entity based on an evaluation of security characteristics of the IP addresses associated with the entity and security characteristics of one or more IP addresses attributed to the one or more remote office networks.
|