| CPC G06F 21/56 (2013.01) [G06F 16/2379 (2019.01); G06F 16/24552 (2019.01); G06F 16/23 (2019.01); G06F 21/552 (2013.01); G06F 21/554 (2013.01); G06F 21/6218 (2013.01); G06F 2221/034 (2013.01)] | 3 Claims |
|
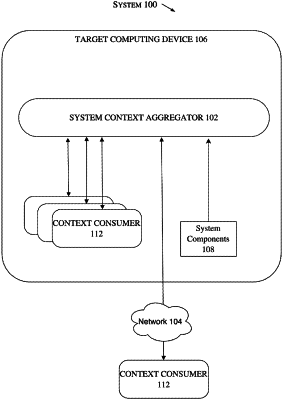
1. A method for detecting malicious activity in a target computing system having a cache storage and a persistent storage, the method comprising:
collecting a system context of a target computing system from one or more system components of the target computing system, wherein the system context comprises a first set of attributes;
storing the system context in the cache storage;
initializing a system context database of the target computing system;
requesting, by a context consumer, the first set of attributes in the cache storage, wherein the context consumer comprises a data security component;
wherein each of the one or more data security components of the context consumer are configured to access the system context in a synchronized manner;
providing the requested first set of attributes to the context consumer if the requested first set of attributes is in the cache storage;
comparing, by the data security component of the context consumer, the requested first set of attributes of the target-computing-system event reporting the presence of malware if the first set of attributes matches the second set of attributes;
storing the first set of attributes of a system event in the persistent storage for backward analysis;
removing the first set of attributes from cache storage; and
restoring the first set of attributes to the cache storage if the context consumer requests the first set of attributes when those attributes are no longer in cache storage.
|