| CPC H04W 12/088 (2021.01) [H04W 12/30 (2021.01)] | 15 Claims |
|
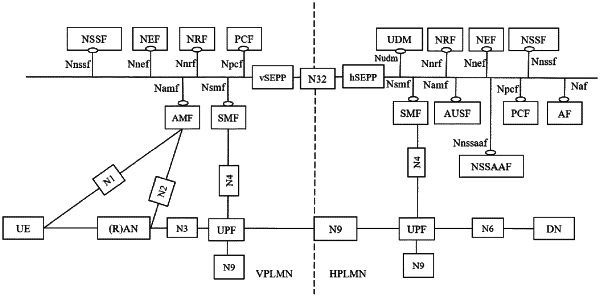
1. A method to enable a-secure data communication between a first network of a first network provider and a second network of a second network provider,
wherein the first network comprises at least a first part that is a 5G communication environment, wherein the second network comprises at least a first part that is a communication environment preceding the 5G communication environment, and wherein an access link to the first part of the second network comprises a GPRS Tunneling Protocol (GTP)-firewall to protect the first part of the second network,
wherein the method comprises the following steps:
establishing a handover process from the 5G communication environment of the first network to the non-5G first part of the second network, in particular to a 4G communication environment of the second network;
directing control plane traffic of the data transmission from a security edge protection proxy (SEPP) of the first network to a SEPP of the second network, wherein the SEPP of the first network encrypts the data transmission and the SEPP of the second network decrypts the encrypted data transmission;
directing user plane traffic of the data transmission to the access link to the non-5G first part of the second network and through the GTP-firewall; and
providing the decrypted control plane traffic to the GTP-firewall, wherein the GTP-firewall performs security measures based on information extracted from the control plane traffic.
|