| CPC H04W 12/04 (2013.01) [G06F 16/9554 (2019.01); G06F 21/445 (2013.01); G06F 21/606 (2013.01); G06K 7/1404 (2013.01); G06K 7/1417 (2013.01); G06K 19/06037 (2013.01); G06Q 20/3274 (2013.01); G06Q 20/3276 (2013.01); H04L 9/0819 (2013.01); H04L 9/0838 (2013.01); H04L 9/0866 (2013.01); H04L 9/0891 (2013.01); H04L 9/3226 (2013.01); H04L 9/3234 (2013.01); H04L 63/18 (2013.01); H04L 67/04 (2013.01); H04L 69/18 (2013.01); H04W 12/03 (2021.01); H04W 12/0471 (2021.01); H04W 12/06 (2013.01); H04W 12/50 (2021.01); H04L 2209/805 (2013.01); H04W 4/80 (2018.02)] | 18 Claims |
|
1. A first communication device for performing secure communications, the first communication device comprising:
one or more processors; and
memory storing instructions that, when executed by the one or more processors, cause the one or more processors to:
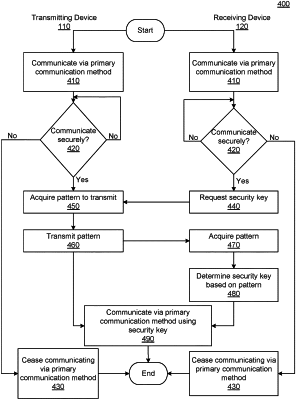
detect a change in a pairing configuration for securely pairing the first communication device and a second communication device;
in response to detecting the change in the pairing configuration, determine that a first security key is to be replaced;
in response to determining the first security key is to be replaced, determine, using a first communication method, that the second communication device is within a range for secure communication based on a detected distance of the second communication device from the first communication device;
in response to determining the second communication device is within the range, (i) transmit a key request to the second communication device via a second communication method, and (ii) receive a sensory pattern via the second communication method, the second communication method being different from the first communication method;
determine, using one or more decoding schemes included by the pairing configuration, a second security key based on the sensory pattern; and
receive encrypted messages via the first communication method and decrypt the encrypted messages using the second security key.
|