| CPC H04L 9/3268 (2013.01) [H04L 9/14 (2013.01); H04L 9/30 (2013.01)] | 20 Claims |
|
1. An Information Handling System (IHS), comprising:
a host processor;
a security processor coupled to the host processor; and
a memory coupled to the security processor, the memory having program instructions stored thereon that, upon execution, cause the security processor to:
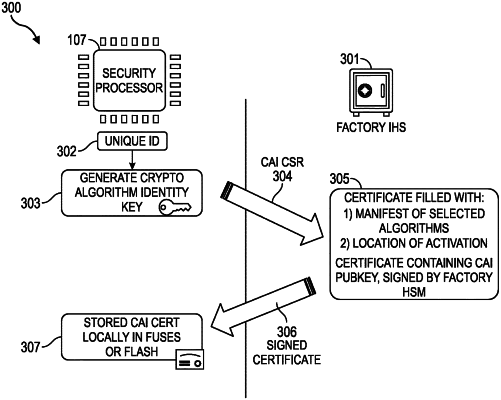
generate a Cryptographic Algorithm Identity (CAI) key pair comprising a CAI public key and a CAI private key;
issue a CAI Certificate Signing Request (CSR) to a factory IHS, wherein the CAI CSR comprises the CAI public key;
receive a signed CAI certificate from the factory IHS, wherein the signed CAI certificate is usable to activate a selected set of regional cryptographic algorithms among a superset of regional cryptographic algorithms stored, during manufacturing of the IHS, in a firmware of the security processor; and
store the signed CAI certificate.
|