| CPC H04L 9/3242 (2013.01) [G06F 11/1004 (2013.01); G06F 21/64 (2013.01); H04L 9/0866 (2013.01)] | 20 Claims |
|
1. A trusted computing device, comprising:
a device driven by firmware; and
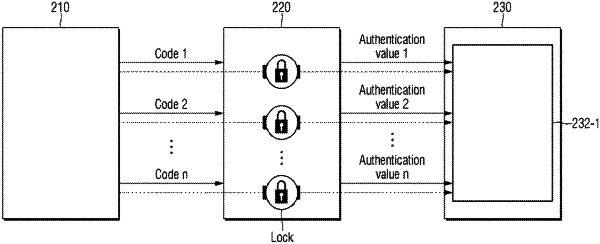
a master controller, which generates an authentication value from the firmware and checks integrity for the authentication value at a first period,
wherein the master controller includes:
an authentication value generator, which generates the authentication value;
an authentication value repository, which stores the authentication value;
a security core, which blocks access to the authentication value stored in the authentication value repository from another core of the master controller or from a source outside the master controller to block modulation for the authentication values; and
an integrity checker, which checks integrity for the authentication value stored in the authentication value repository.
|