| CPC H04L 63/1466 (2013.01) [H04L 12/4641 (2013.01); H04L 63/1416 (2013.01)] | 16 Claims |
|
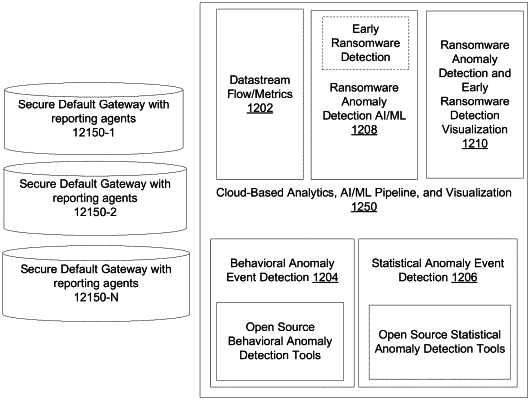
1. A method for ransomware protection in a Virtual Local Area Network (VLAN), comprising:
deploying at least one gateway with each gateway having point-to-point links with a plurality of client endpoint devices, with each gateway having a security appliance acting as a DHCP relay assigning itself as the default gateway to a plurality of client endpoint devices in a VLAN after receiving a DHCP response wherein the security appliance overwrites a subnet mask to 255.255.255.255 to set the security appliance as a default gateway for the plurality of endpoint devices of the VLAN; and
sending a copy of message traffic of the gateway to an early ransomware detection system to analyze network traffic from each of the at least one gateway for behavioral anomalies and statistical anomalies.
|