| CPC H04L 63/145 (2013.01) [H04L 63/0227 (2013.01); H04L 63/1416 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
1. A system for threat detection, the system comprising:
a malware detection engine executing on an endpoint in an enterprise network, the malware detection engine configured to detect a security violation including an instance of an advanced persistent threat on the endpoint; and
a threat management facility for managing the enterprise network, the threat management facility coupled in a communicating relationship with the endpoint and configured to:
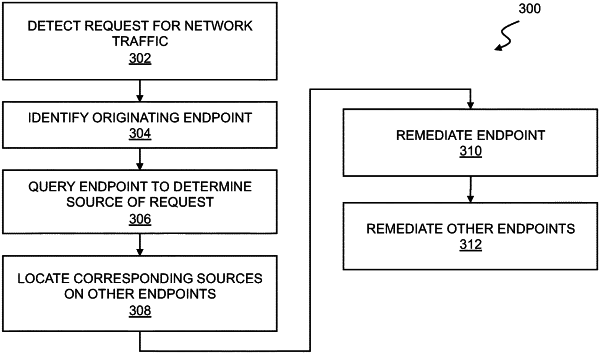
receive a report of the security violation from the malware detection engine,
identify the endpoint associated with the malware detection engine that reports the security violation,
query the endpoint to determine a first instance of a source of the security violation on the endpoint,
identify one or more other endpoints associated with the enterprise network that contain a second instance of the source of the security violation, and
cause the one or more other endpoints to remediate the second instance of the source on the one or more other endpoints.
|