| CPC H04L 63/1433 (2013.01) [H04L 63/14 (2013.01); H04L 63/1441 (2013.01); H04L 63/20 (2013.01); G06F 21/577 (2013.01)] | 20 Claims |
|
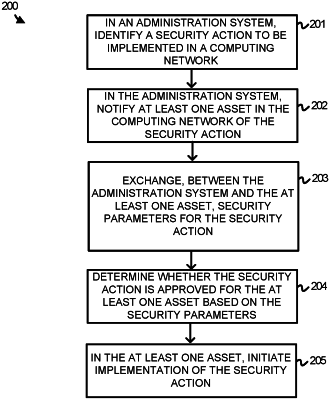
1. A computer-implemented method comprising:
identifying a security threat in a computing network monitored by an administration system for instances of security threats;
identifying a first security action to execute at a first computing asset of the computing network and a second security action to execute at a second computing asset of the computing network, wherein each of the first security action and the second security action are specified using a unified security language supported by the administration system, wherein each of the first security action and the second security action, when executed, mitigates an effect of the security threat in the computing network, and wherein the first security action includes one or more of: blocking an internet protocol (IP) address, removing a process from the first computing asset, segregating the first computing asset from other computing assets in the computing network, or preventing access to the first computing asset by a user;
in response to identifying the first security action to execute at the first computing asset and the second security action to execute at the second computing asset, causing a credential interface to be displayed;
receiving, by the administration system via the credential interface, first credentials associated with the first computing asset, wherein the first computing asset is a first type of computing asset;
receiving, by the administration system via the credential interface, second credentials associated with the second computing asset, wherein the second computing asset is a second type of computing asset that is different from the first type of computing asset;
sending, by the administration system to the first computing asset, a first request to execute the first security action, wherein the first request includes the first credentials associated with the first computing asset;
sending, by the administration system to the second computing asset, a second request to execute the second security action, wherein the second request includes the second credentials associated with the second computing asset;
authorizing, by the first computing asset, the first credentials associated with the first computing asset to enable the first computing asset to determine that the first security action is permitted; and
authorizing, by the second computing asset, the second credentials associated with the second computing asset to enable the second computing asset to determine that the second security action is permitted.
|