| CPC H04L 63/1433 (2013.01) [G06F 16/955 (2019.01); H04L 61/4511 (2022.05); H04W 24/08 (2013.01); H04W 72/51 (2023.01); H04W 80/10 (2013.01)] | 20 Claims |
|
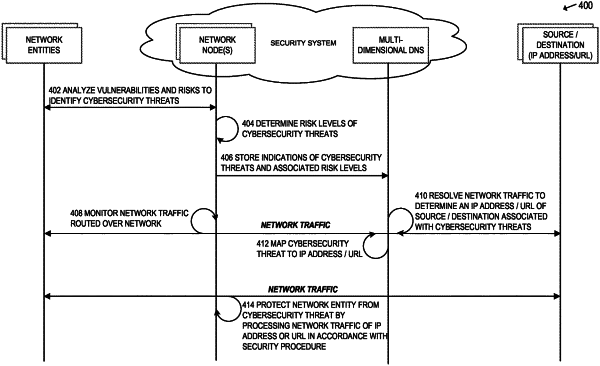
1. At least one computer-readable storage medium, excluding transitory signals and carrying instructions, which, when executed by at least one data processor of a security system, cause the security system to:
monitor, by a computing resource of the security system, network traffic routed via a 5G network;
resolve, with a Domain Name System (DNS) that is communicatively coupled to the 5G network, the network traffic to determine an address of an endpoint of the network traffic;
in response to determining the address of the endpoint of the network traffic, determine, based on information stored in the DNS, that the address is associated with a cybersecurity threat;
in response to determining that the address is associated with the cybersecurity threat, determine, from a range of risk levels, a risk level stored in the DNS in association with the address;
responsive to determining the risk level associated with the address, provide, to a network entity and based on the address being associated with the cybersecurity threat, a digital coupon to perform a security procedure to protect the network entity from the cybersecurity threat,
wherein the security procedure is selected from multiple security procedures based on the risk level;
receive, from the network entity, an indication of acceptance of the digital coupon to perform the security procedure; and
in response to receiving the indication of acceptance of the digital coupon, protect the network entity from the cybersecurity threat by processing the network traffic in accordance with the security procedure.
|