| CPC H04L 63/126 (2013.01) [G06F 21/57 (2013.01); H04L 63/08 (2013.01); G06F 2221/2115 (2013.01)] | 7 Claims |
|
1. A method for identity proofing a user entity to allow for a transaction request comprising:
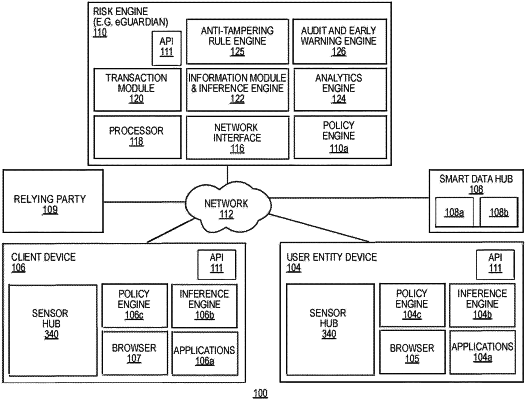
in a resolution step, capturing registration information of the user entity and a user entity device at a relying party and after the registration information is received from the relying party at a risk engine, monitoring the user entity by the risk engine to collect contextual and behavioral data of the user entity during an active session;
in a first part of a validation step, determining by the risk engine whether the user entity is not a threat actor by reviewing a plurality of egocentric and allocentric factors of the user entity and the user entity device and if an abnormality is detected, notifying the relying party to terminate the active session;
in a second part of the validation step, reviewing by the risk engine evidence submitted by the user entity and comparing the evidence to a database to determine whether the user entity is genuine and whether the user entity is a claimed registered identity or a new identity, retrieving a bio-behavioral model of the user entity and updating the bio-behavioral model with the contextual and behavioral data of the user entity to form an updated bio-behavioral model and comparing the plurality of egocentric and allocentric factors of the transaction request with the update bio-behavioral model to determine the level of abnormalties associated with the transaction request and determine a risk score;
in the verification step, if the user entity is the claimed registered identity, the risk engine already has contact information for the user entity and contacts the user entity directly through a predetermined out of band notification and if the user entity is a new identity, obtaining the contact information for the user entity from at least one of a plurality of third party data sources and contacting the user entity to obtain a confirmation that the user entity is attempting to register with the relying party; and
sending from the risk engine to the relying party a risk score determining whether the user entity is a threat actor.
|