| CPC H04L 63/101 (2013.01) [G06F 16/2255 (2019.01)] | 20 Claims |
|
1. A method comprising:
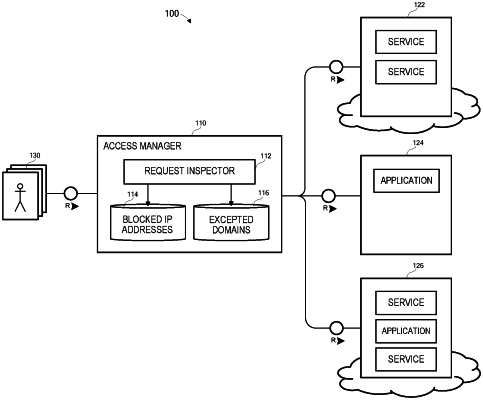
receiving a request for access to a target domain, the request including a source Internet Protocol (IP) address;
determining whether the source IP address is one of a plurality of IP addresses indicated within stored first data, the stored first data indicating the plurality of IP addresses are designated as a blocked IP address;
in response to determining the source IP address is one of the plurality of stored IP addresses, determining whether the target domain is one of a plurality of domains indicated within stored second data, the stored second data indicating the plurality of domains are designated as an excepted target domain of at least one of an application and a service;
in response to determining the source IP address is one of the plurality of IP addresses indicated within the stored first data and the target domain is one of a plurality of domains indicated within the stored second data, forwarding the request to the target domain;
accessing a log record associated with the request, the log record indicating the source IP address, the target domain, and a disposition of the request;
determining a second plurality of IP addresses of a stored third data at a time of the request and a second plurality of domains of a stored fourth data at the time of the request, the stored third data indicating the plurality of IP addresses designated as a blocked IP address at the time of the request and the stored fourth data indicating the plurality of domains designated as an excepted target domain of at least one of an application and service at the time of the request;
evaluating the disposition of the request against the second plurality of IP addresses of the stored third data at the time of the request and the second plurality of domains of the stored fourth data at the time of the request;
generating a first hash of the stored third data;
comparing the first hash to a stored second hash corresponding to the stored first data; and
in an instance the first hash is not identical to the stored second hash, updating the stored first data based on the stored third data.
|