| CPC H04L 63/083 (2013.01) [G06F 21/45 (2013.01); H04L 9/14 (2013.01); H04L 63/0478 (2013.01)] | 20 Claims |
|
1. A system for setting up a wallet for a decentralized application by performing non-custodial authentication for a client, the system comprising:
processing circuitry; and
a memory operably coupled to the processing circuitry, having embodied thereon a program, the program being readable by processing circuitry and, when executed, causes the processing circuitry to:
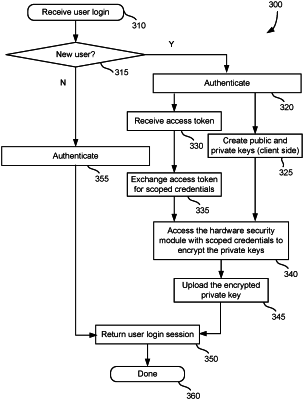
receive over a network, a request for an access token for a user, at a first computing environment, from a second computing environment that authenticated the user;
send over the network, the access token for the user, from the first computing environment, to the second computing environment;
receive over the network, the access token, at the first computing environment, bypassing the second computing environment, from a third computing environment;
receive over the network, key information that is generated within a fourth computing environment at the third computing environment, the fourth computing environment is inaccessible to the decentralized application at the third computing environment, at the first computing environment, bypassing the second computing environment, from the third computing environment; and
send the key information from the first computing environment to a security resource to cause the security resource to encrypt the key information to generate encrypted key information.
|