| CPC H04L 63/0823 (2013.01) [H04L 63/02 (2013.01); H04L 63/0209 (2013.01); H04L 63/029 (2013.01); H04L 63/0428 (2013.01); H04L 63/10 (2013.01); H04L 63/126 (2013.01); H04L 67/01 (2022.05); H04L 67/125 (2013.01); H04L 67/141 (2013.01); H04L 63/166 (2013.01)] | 18 Claims |
|
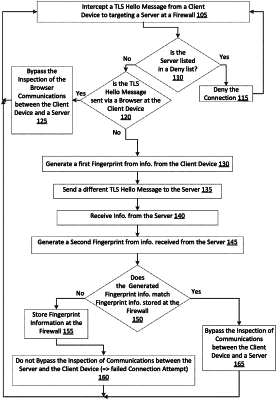
1. A method for bypassing one or more processes at computing devices, the method comprising:
intercepting a request at a firewall, the request sent from a computing device to initiate establishment of a secure communication session with a server and access to application program data stored at the server;
identifying whether the request is from an Internet browser of the computing device;
generating a first attribute at the firewall based on information in the request from the computing device, the information in the request including computing device identification information, wherein the first attribute is also generated based on the identification whether the request was sent from the Internet browser;
generating a second attribute at the firewall based on information received from the server in response to an access request that included the first attribute sent to the server from the firewall, wherein the second attribute is generated based on the information including server identification information;
identifying that the secure communication session is allowed to be established based on the first and the second attribute corresponding to a plurality of additional attributes previously stored at the firewall;
bypassing inspection of a second request at the firewall based on a first fingerprint and a second fingerprint associated with the first and second attributes matching attributes stored at a data store to allow communications between the computing device and the server; and
allowing a subsequent secure communication session to be established between the server and the computing device.
|